In the process of setting up secure DNS (Domain Name System) for the ipv6security.nl domain, I found out that my workstation was not able to use this additional security feature. With secure DNS transactions (DNSSEC) you will benefit from the fact that no one can tamper the name-to-address translation (DNS), so you will connect to the correct system in stead of a fake or man-in-the-middle (MITM) system.
There are three parts to it, which should work together:
- Authoritative DNS server, holding the RR-records for name to IP resolution or visa-versa
- Resolver DNS server, resolving queries on behave of clients
- Client resolver, querying the Resolver DNS for name to IP translation or visa-versa
Step 1. is currently work in progress, by which SIDN (Dutch Domain Registration Authority) did validate the ipv6security.nl domain and will include the DS RR-record in the nl. TLD soon.
Step 3. is part of modern Operating Systems and will probably work for you
Step 2. turned out to be an issue at my place, for which I had to make some changes to get it to work.
How to enable DNSSEC validation with BIND?
Note: the dnssec-validation option is only supported on BIND v9.4 or above, on v9.3 the dnssec-enable option covers validation as well.
You have to tell your DNS server to do DNSSEC validation checks, by enabling it in the named.conf configuration file. Put it in the “options” section.
options {
dnssec-validation yes;
};
BIND will now attempt DNSSEC validation, which relies on a chain-of-trust untill it reaches a trused authority. In my case this SEP (Secure Entry Point) was missing in my named.conf file. Adding this trust-anchor can simply be done by obtaining the DNSKEY of the “.” domain with the dig command.
dig . DNSKEY
You will get two public keys called 256 (ZSK) and 257 (KSK), of which you have to add the section with 257 in the named.conf file. I have to mention that obtaining the “root” DNSKEY via dig is not 100% secure and checking it against another way of obtaining it should be considered.
trusted-keys {
"." 257 3 8 "AwEAAag........" ;
};
Restart BIND and you should have a DNSSEC validating enabled DNS server.
An excellent way to validate if DNSSEC validation is working properly, is to go to SIDN DNSSEC validation page which should give you a green “You are protected” check mark as shown below.
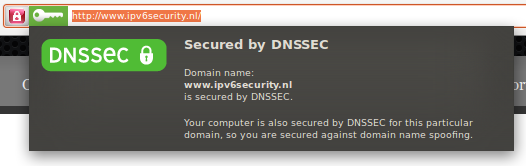
How do I see that I had a secure DNS transaction?
An easy and simple why to indicate that you’re browsing on a website translated by DNSSEC, is by installing the FireFox DNSSEC Validator plug-in. You will get a collored key in the address bar, in front of the URL.