Following the Snowden leaks revealing Bullrun – the NSA program to crack the world’s encryption – there is an emerging consensus that users can no longer automatically trust any security.
Cryptographer and EFF board member Bruce Schneier has given advice on how to be as secure as possible. “Trust the math,” he says. “Encryption is your friend. Use it well, and do your best to ensure that nothing can compromise it. That’s how you can remain secure even in the face of the NSA.”
He confirms the growing consensus that Bullrun‘s greatest success is in subverting the implementations of encryption rather than in the ability to crack the encryption algorithms themselves. The general belief is that the NSA has persuaded, forced or possibly even tricked individual companies into building weaknesses or backdoors into their products that can be exploited later.
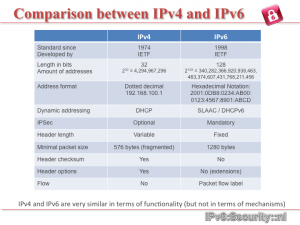
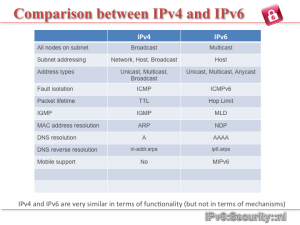
The bottom line, however, is that the fabric of the internet can no longer be trusted. Meanwhile, John Gilmore, co-founder of EFF and a proponent of free open source software, has raised a tricky question: has NSA involvement in IPv6 and IPSEC discussions effectively downgraded its security? IPSEC is the technology that would make IP communications secure.
Gilmore notes that he had been involved in trying to make IPSEC “so usable that it would be used by default throughout the internet.” But “NSA employees participated throughout, and occupied leadership roles in the committee and among the editors of the documents.”
The result was “so complex that every real cryptographer who tried to analyze it threw up their hands and said, ‘We can’t even begin to evaluate its security unless you simplify it radically'” – something that never happened.
Gilmore doesn’t explicitly say that the NSA sabotaged IPSEC, but the fact remains that in December 2011, IPSEC in IPv6 was downgraded from ‘must include’ to a ‘should include.’ He does, however, make very clear his belief in NSA involvement in other security standards.
Discussing cellphone encryption, he says “NSA employees explicitly lied to standards committees” leading to “encryption designed by a clueless Motorola employee.”
To this day, he adds, “no mobile telephone standards committee has considered or adopted any end-to-end (phone-to-phone) privacy protocols. This is because the big companies involved, huge telcos, are all in bed with NSA to make damn sure that working end-to-end encryption never becomes the default on mobile phones.”